This article describes key IT security auditing techniques available in Windows, such as auditing and advanced auditing of GPOs, event log ...
Event Log, Audit Log and Syslog messages have always been a good source of troubleshooting and diagnostic information, but the need to back up audit trail .... The events are written to the Windows system event log and can be examined using the Event Viewer. Auditing provides a way for an .... Produces auditing on file paths, registry keys and processes with pre-existing audit permissions. Detects some forms of unauthorised changes to ...
event auditing
event auditing, event auditing services, windows event auditing, active directory event auditing, subsequent event auditing, windows 10 event auditing, security event auditing, netiq event auditing service, subsequent events auditing standards, system events auditing, auditing event python, auditing event viewer, auditing event logs, auditing event meaning, auditing event id 4663, auditing event 5156, auditing event 4662 Portable PS2 With A Side Of Pi
Jump to Configure Event Log Size and Retention Settings - Monitor These Events for Compromise; Centralize Event Logs; Audit Policy Benchmarks .... Resource Custodians must maintain, monitor, and analyze security audit logs for covered devices. Description of Risk. Without appropriate audit logging, an .... This holds true for Windows audit logs in particular because of the valuable security information they carry. In addition to bolstering security, periodic log auditing is ... Steemt die Kohle

windows event auditing
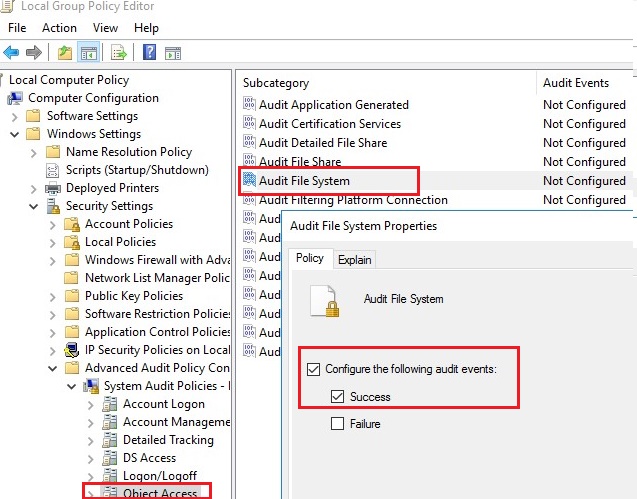
After you enable Active Directory auditing, Windows Server writes events to the Security log on the domain controller. The security event log registers the .... In this first article of a two-part series about event-log auditing, I step you through a script that dumps the Security logs for specified servers and saves the output .... Audit process tracking; Audit system events. An event in the Windows Security log has a keyword for either Audit Success or Audit Failure. When you enable an .... The Security Log, in Microsoft Windows, is a log that contains records of login/logout activity or other security-related events specified by the system's audit policy .... A user who is assigned this user right can also view and clear the Security log in Event Viewer. For more info about the Object Access audit policy ... Octogeddon MULTi3-SiMPLEX
subsequent event auditing
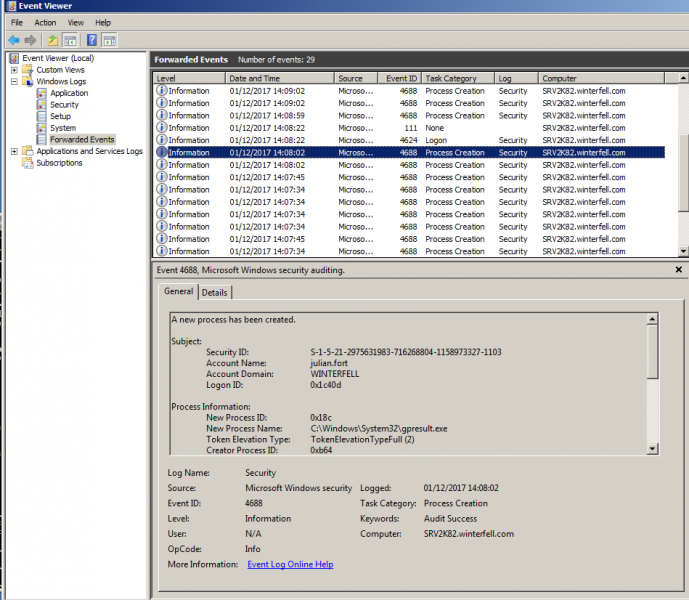
Second, most compliance initiatives request that your organization performs some form of auditing on your event logs. The infamous NIST 800–53, commonly cited .... Audit logs capture events, showing “who” did “what” activity and “how” the system behaved. Here's how to use them as a resource for security .... You can use audit event logs to determine whether you have adequate file security and whether there have been improper file and folder access attempts.. In any enterprise using file servers to store and share data, auditing is important to ensure data security. You can monitor multiple file servers in your domain.. Jump to Windows Event Log Limitations - Once you have enabled the Auditing GPO and set the file/folder auditing, you will see audit events in the Security .... Jump to Log Collector Examples - The first matching rule sets the “audit level” of the event. The known audit levels are: None - don't log events that match .... To enable security audit policy to capture load failures in the audit logs, follow these steps: Open an elevated Command Prompt window.. To maintain a secure network, you must audit server and workstation activity and examine event logs frequently for signs of intrusion or unexpected events. 82abd11c16 [EXCLUSIVE] Time Based Content For WPBakery Page Builder